We Make Digital Products More Secure!
We are a rising company in the Information Security field providing professional cyber security services to many high-profile businesses and leading start-ups to help them secure their web services, mobile applications, and cloud infrastructure..

How Do We Work?
We make sure every step takes its time and we take a methodological approach to achieve that.
Reconnaissance
This process begins with detailed scanning and research into the architecture and environment.
Identify Weaknesses
We use both vulnerability scanning tools and manual analysis to identify security flaws.
Assessment Reporting
We deliver a detailed analysis and threat report, including remediation steps.
Optional Remediation
As an optional addition, we provide remediation retesting for all vulnerabilities listed in the report.
Services & Solutions
We at ASPAAR, continuously strive to provide you with a service that exceeds your expectations.
Infrastructure Penetration Testing
An Infrastructure penetration testing assessment uncovers vulnerabilities residing in your IT systems and provides a tailored approach to each environment.
Web Penetration Testing
We have a variety of advanced penetration testing methodologies that we apply against your web application to insure you the best results, also we focus on the OWASP top 10 vulnerabilities for web applications.
Mobile Penetration Testing
Our method involves an end to end testing of mobile applications on iOS, Android, and Windows Mobile platforms, and seeks to identify and exploit vulnerabilities present within these platforms.
API Penetration Testing
API Penetration Test is an authorized hacking attempt aimed at identifying and exploiting vulnerabilities in the architecture and configuration of a web service.
Cybersecurity Training
Cybersecurity Awareness programs provide an extensive set of security awareness services to train corporate executives and secure their data.
Source Code Review
Modern websites and applications are feature-rich, which make them more susceptible to flaws. Therefore our service is to discover hidden vulnerabilities, design flaws, and verify if key security controls are implemented.
Acknowledged by the leading companies in the world.
Some of Our Customers:
Our Competencies
We're making the following actions for more security of our customers.

The penetration testing report we issue for our customers can be easily imported with one click to most of SDLC workflow such as Jira, Github, Gitlab, Trello.
Once the engagement started, we open a real-time communication channel between the customer and our team members to make sure we have a very smooth connection together. This communication channel doesn't have a specified expiration time. We'll be available all the time on this channel as long the customer have any questions or concerns regarding the findings or the penetration testing engagement in general.
Upon the client's request, we may encrypt the penetration testing report and destroy all engagement results from our side making them unrecoverable for more safety and security for our customers.
Any critical security vulnerabilities that will be discovered during our security assessment is being immediately reported to the client on an initial report through our opened communication channel or any other secure way that client might choose.
We prefer to not conduct our penetration tests on the customer production environment. And we're considerating similar behaviors to avoid anything that could lead to disturbing the business servability. We're performing all of our tests on dedicated environments that have been already prepared by the client before. ("e.g prelive/staging.")
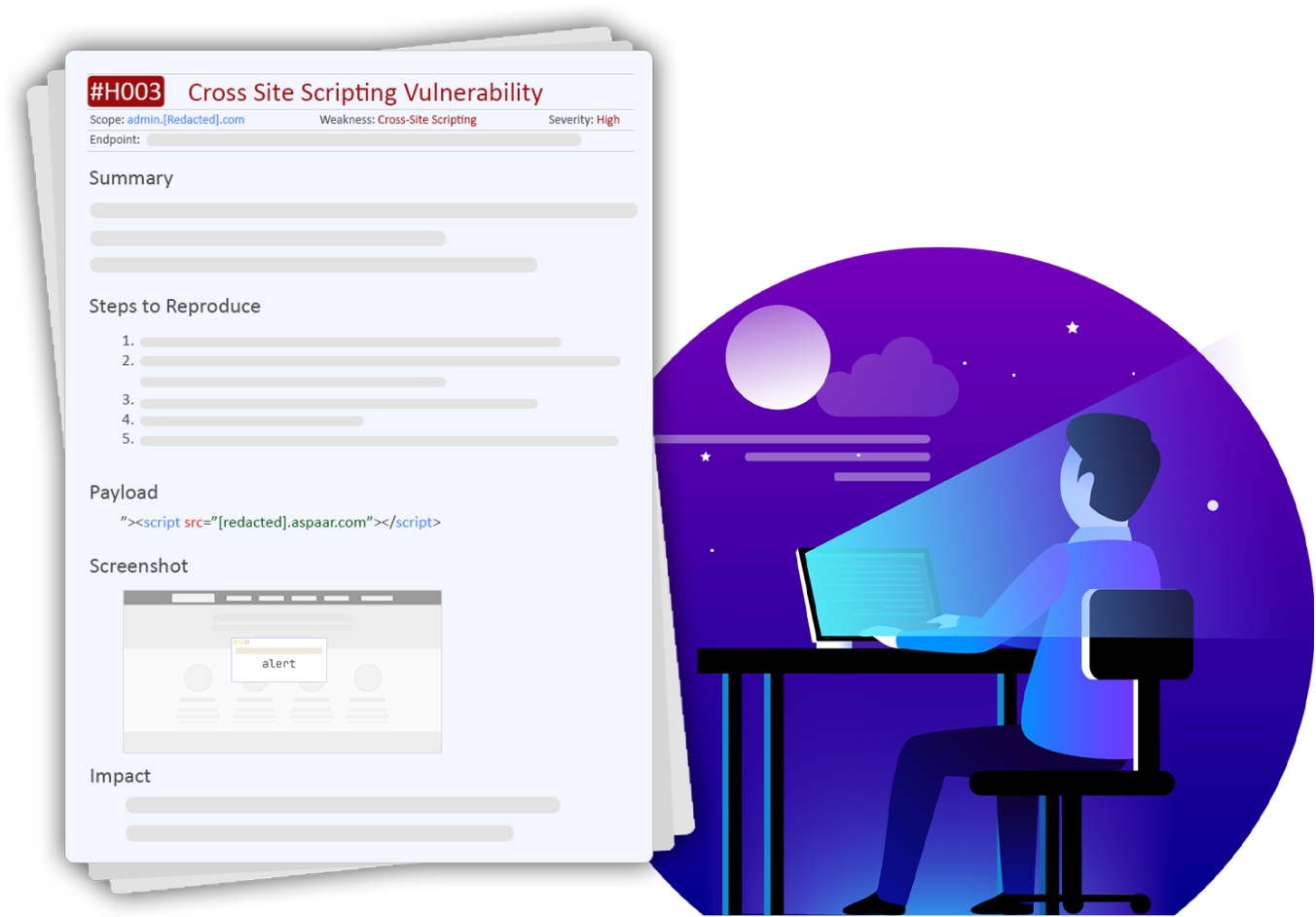
Assessment Reporting
- Executive Summary
- Strategic Strengths and Weaknesses
- Identified Vulnerabilities and Risk Ratings
- Detailed Risk Remediation Steps
- Assets and Data Compromised During Assessment
Talk with a Security Expert
Carry out business as usual with confidence while Aspaar detects, protects, and eliminates any digital threats.
Let's Chat